India, January 20, 2026: Google is reportedly preparing to introduce a new security layer on Android that aims to protect users when installing apps from sources outside the official Play Store, a move that could reshape the way sideloading works on certified Android devices. This emerged from recent reports suggesting Google is adding developer verification and additional checks to enhance user safety against malware and scams.
What Google’s New Security Layer Means
Android has long allowed users to install apps manually through sideloading — downloading and installing app files (APK) from websites, third-party stores or other sources outside Google Play. While this flexibility is a hallmark of the platform’s openness, it also carries security risks, since harmful or malicious apps are far more common outside official app marketplaces.
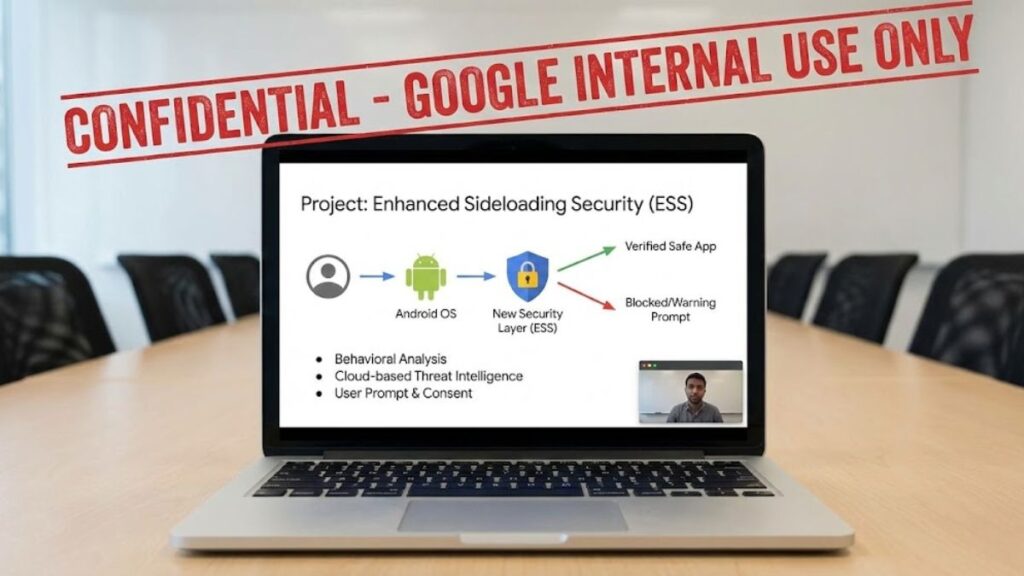
According to reports, Google is adding an extra verification step that will prompt users and developers during the installation process. This layer is reportedly being built into the Play Store and Android system to confirm the developer identity behind an app before installation, even for sideloaded packages.
Under this proposed model:
- Google will check whether the app installer and developer are verified before allowing installation.
- Users may see additional warnings and security prompts, especially when trying to install apps from unverified or unknown sources.
- In some cases, users may still be able to proceed with installation after acknowledging risks, but the process will be more high friction and security-focused.
This verification approach is similar to recent Android policies that require developers to register and prove their identity before distributing apps — a change originally announced by Google to protect users from malicious installations, financial malware and scams.
Developer Verification and Open Debate
The emerging policy builds on Google’s earlier strategy to require developer identity verification for all Android apps installed on certified devices. That initiative aims to make it harder for bad actors to repeatedly publish harmful software by attaching real-world identity to app publishers. The verification process is set to expand in phases starting from 2026 in select regions and globally thereafter.
However, this step has been controversial. Some security experts and developers welcomed the added layer of accountability, noting that sideloaded apps have historically been a common vector for malware. But others warn that this risks limiting Android’s openness and could make it harder for independent developers and hobbyists to share software freely.
Reports also indicate that Google may soften enforcement for experienced users, allowing them to proceed with installations after seeing strong risk warnings — a compromise between security and freedom for power users.
Impact on Users and App Distribution
For everyday users, this new security layer will likely enhance protection against malicious apps, phishing campaigns and malware installed through sideloaded APK files. Android has historically seen many more security threats via sideloading compared with official Play Store installations, prompting the need for stronger safeguards.
At the same time, the changes could have ramifications for alternative app marketplaces, third-party distribution channels and open-source communities that rely on sideloading as a major distribution path. Developers sharing apps outside traditional channels may need to complete identity verification or face additional hurdles.
Why Google Is Taking This Step
The push toward stronger sideloading security reflects broader concerns about mobile malware, scams and financial fraud that exploit unrestricted app installations. By associating apps with verified developer identities and introducing high-visibility warnings during installation, Google hopes to reduce the spread of harmful software without eliminating the ability to sideload entirely.
This development is part of a larger security focus in Android, including other features like Play Integrity API checks and protections against known malware vectors, reinforcing the platform’s defenses against increasingly sophisticated threats.